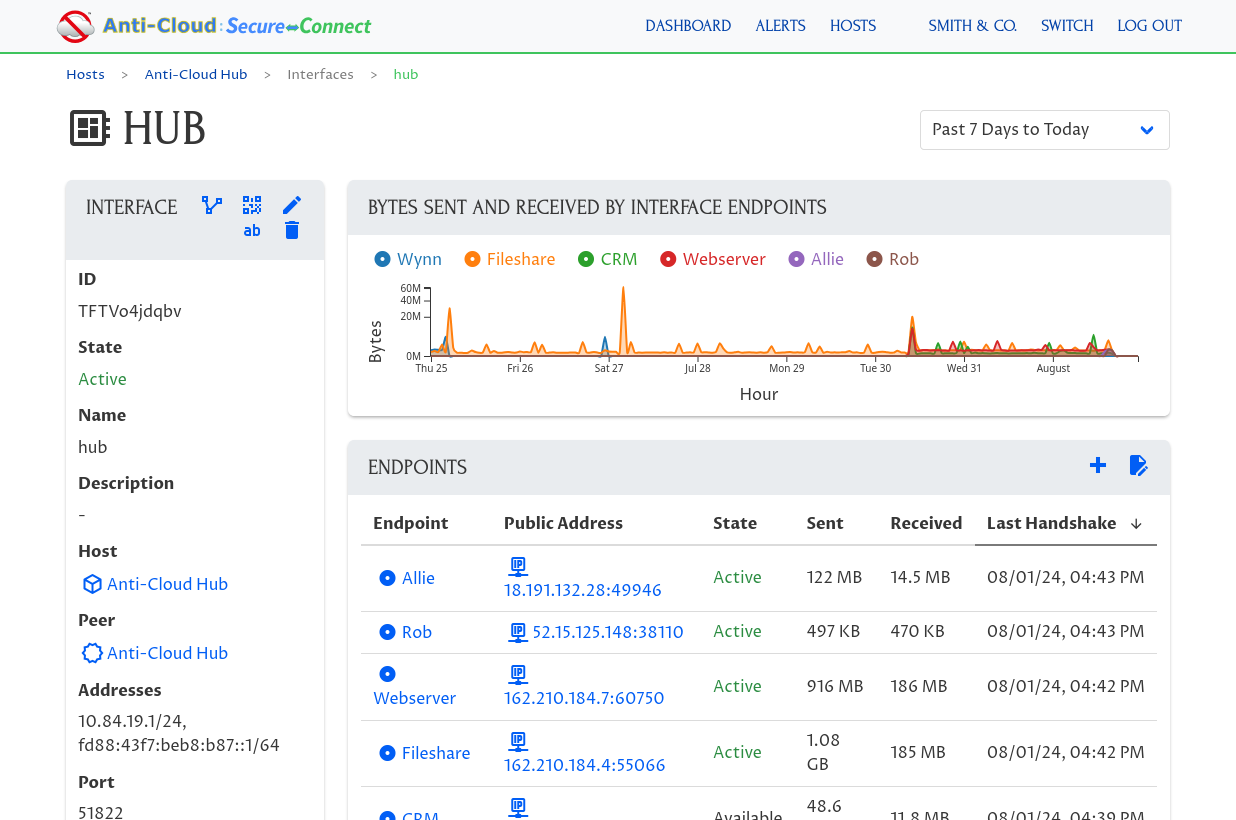
:
: 
 :
:  (ACSC) is a Secure Network as a Service (SNaaS). ACSC makes it easy to set up your own private secure network (or multiple private secure networks). ACSC also includes a number of features that makes it easy for Managed Service Providers (MSPs) to manage individual private secure networks for their clients.
(ACSC) is a Secure Network as a Service (SNaaS). ACSC makes it easy to set up your own private secure network (or multiple private secure networks). ACSC also includes a number of features that makes it easy for Managed Service Providers (MSPs) to manage individual private secure networks for their clients.
Benefits
- ACSC provides high performance secure data transport over any network.
- ACSC ensures the right users have the right access to the right systems.
- ACSC blocks cybersecurity breaches and other incidents.
- ACSC enables you to meet HIPAA, PCI and other compliance requirements.
- ACSC gives you control and visibility into your own private secure network.
High Performance Secure Networking
ACSC provides high performance secure data transport over any network.
ACSC is easy to use, fast and secure. It uses WireGuard for modern, fast and quantum-safe encryption and authentication. On top of WireGuard, ACSC adds a host of additional features, including optimized data transport, advanced authentication and authorization and the ability to create arbitrary network topologies with minimal configuration.
ACSC enables you to easily create multiple private secure networks. Each private network is fully segregated from all other networks, giving you full control over who has access to it (and within it) -- and strictly blocking everyone else. Each device added to the network automatically uses the fast & secure ACSC Network in place of its local network connection.
Let the Right Users In
ACSC ensures the right users have the right access to the right systems.
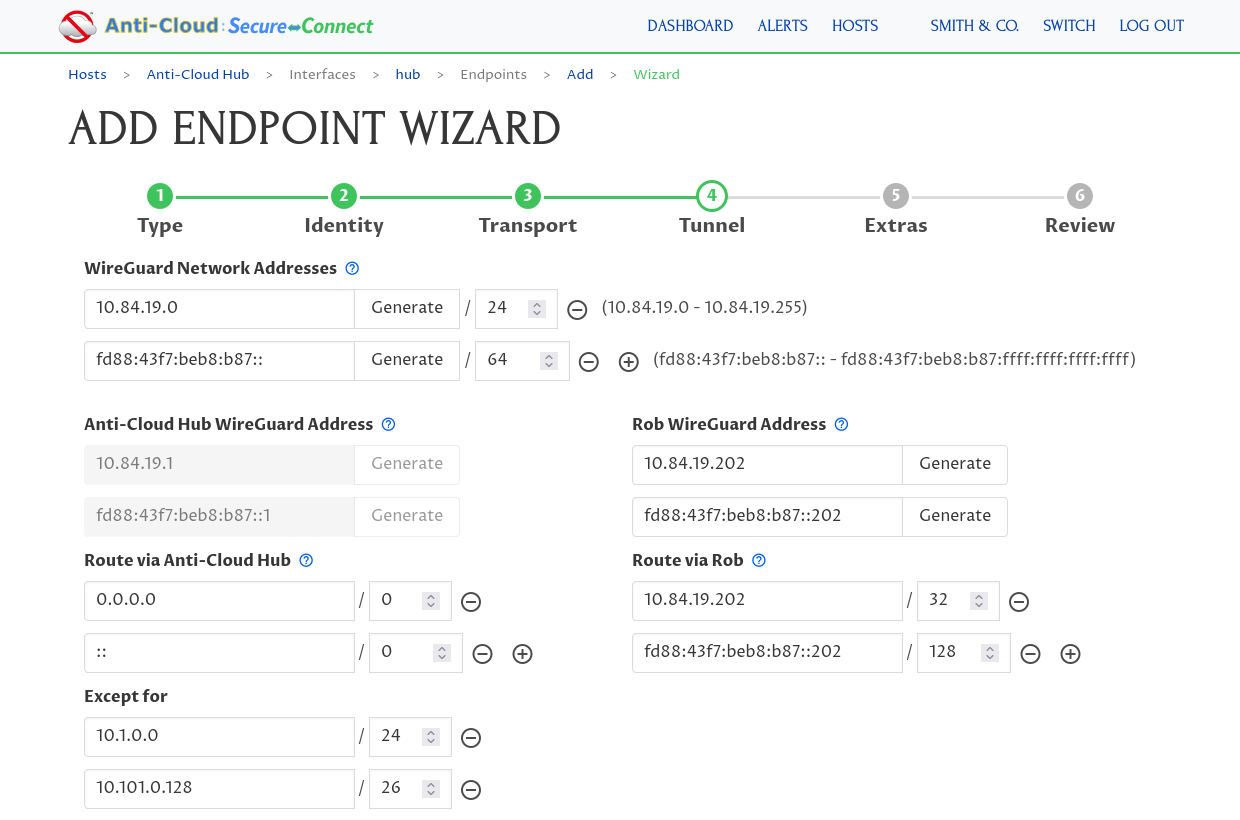
You can add any device from any network or geographic location to the ACSC Network. Simply authorize the device in the ACS Management UI, then install the ACSC Agent and configuration on the device. The same ACSC Agent and enrollment process can be used on an end-user workstation, on-premises server, Internet of Things (IoT) device, or cloud Virtual Machine (VM).
Once enrolled, the device will automatically use the fast & secure ACSC Network in place of its local network connection. This allows authorized users to access network services through the ACSC Network from anywhere and blocks all other access. You can use the ACSC Management UI to apply further fine-grained access control, enable temporary access, or fully and immediately revoke access to your private secure network.
Keep the Bad Guys Out
ACSC blocks cybersecurity breaches and other incidents.
According to the 2024 Verizon Data Breach Investigations Report, approximately 75% of cybersecurity data breaches occurred due to weak or stolen credentials, phishing, or server or application vulnerabilities. ACSC virtually eliminates these attack vectors.
Once you protect a device by enrolling it into ACSC, the device can be accessed remotely only through your private secure ACSC Network. ACSC prevents attackers from exploiting vulnerable devices -- as well as vulnerable applications running on the devices -- by blocking network access to them. Weak, stolen, or phished credentials cannot be used against devices if attackers can not access them; nor can other device or application vulnerabilities be exploited.
Furthermore, the credentials used by ACSC itself are 256-bit keys, generated randomly, never reused and rotated frequently. These credentials are immune to brute-forcing and credential-stuffing attacks. At your option, you can also require Multi-Factor Authentication (MFA) or smart cards to be present in order to use your private secure ACSC Network, making ACSC credentials fully theft-resistant.
Foundational Security Controls
ACSC enables you to meet HIPAA, PCI and other compliance requirements, such as for Cyber Liability Insurance.
ACSC provides foundational network security controls that are the cornerstone of any security plan. ACSC enforces Zero Trust Network Access (ZTNA), allowing you to meet your policy requirements with powerful technical controls.
- ACSC secures all network traffic between enrolled devices, using encrypted connections with mutual authentication.
- ACSC authentication always requires 256-bit keys, generated randomly, never reused and rotated frequently.
- ACSC can optionally require MFA or smart cards for maximum security.
- ACSC limits network access using the principle of least privilege.
- ACSC enforces cryptokey routing, binding each ACSC identity to a unique private IP address.
- ACSC monitors and logs all network traffic.
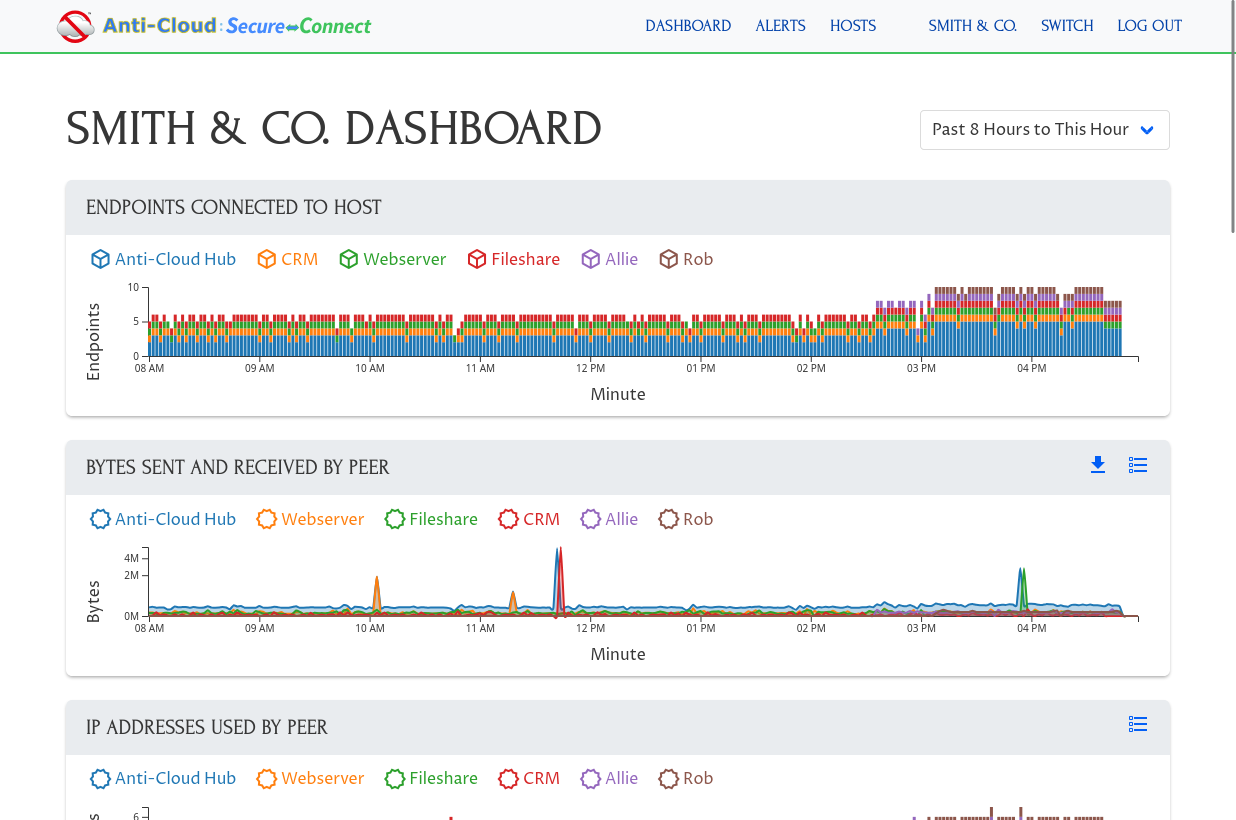
Visibility and Insight
ACSC gives you control and visibility into your own private secure network.
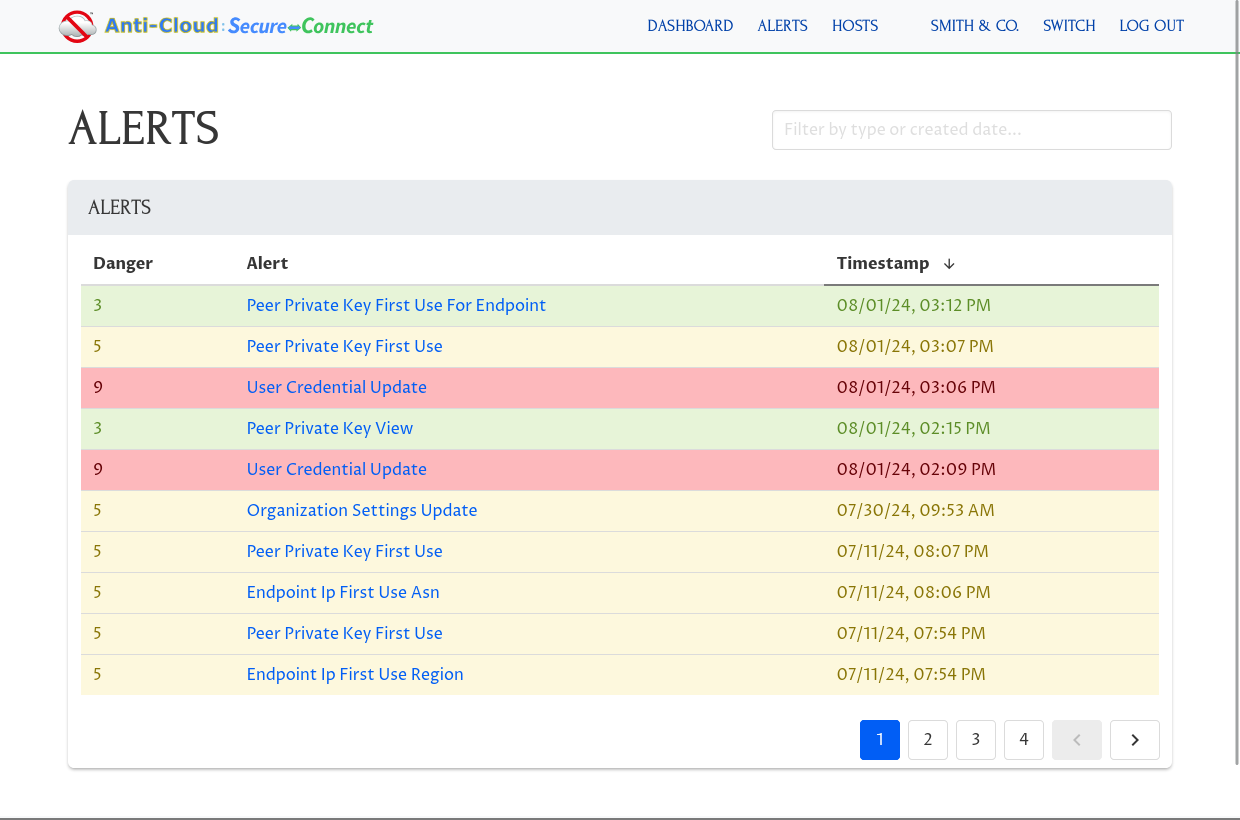
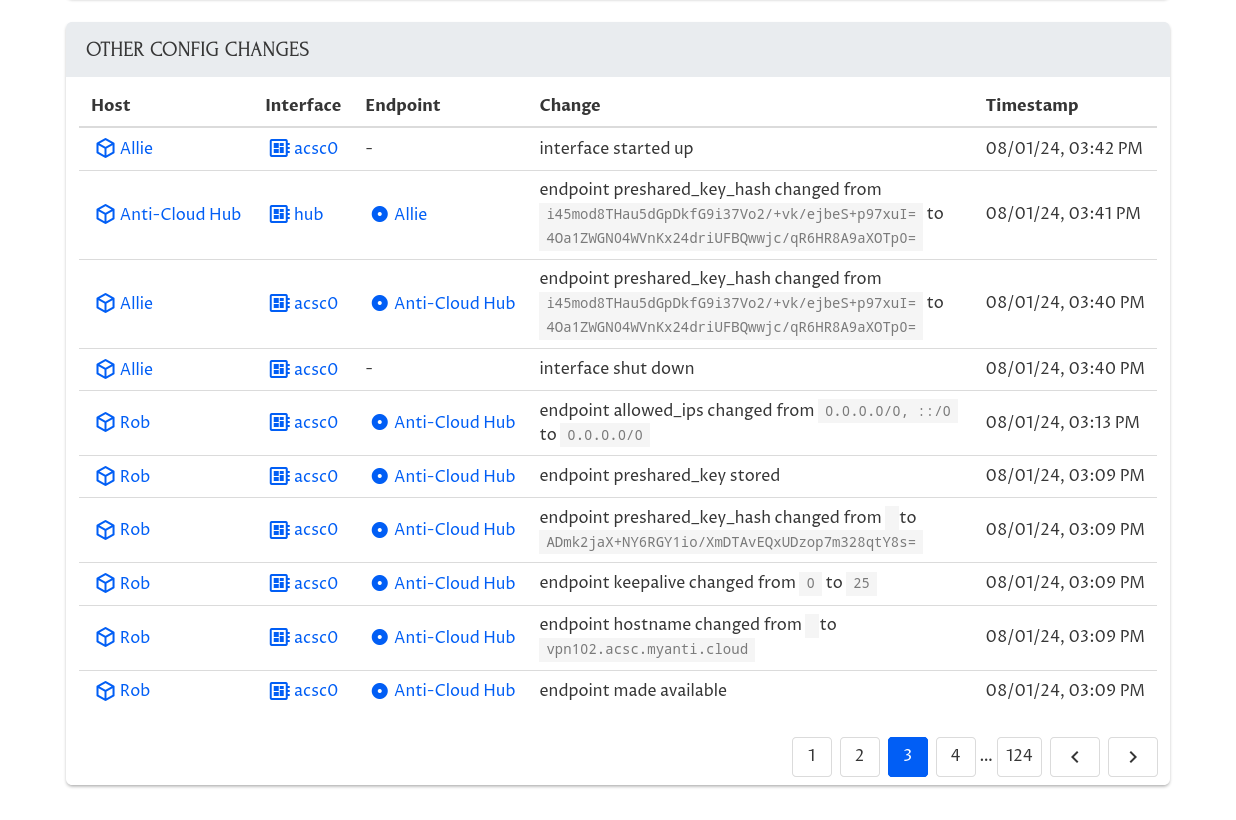
ACSC makes it easy to control and verify who has access to your internal applications and systems. ACSC automatically logs all network access, as well as all changes to your ACSC Network. You can rollback any changes easily and block access to any unauthorized users immediately.
ACSC will also proactively alert you of suspicious network activity or access. ACSC logging and alerts can be integrated into your own logging, analytics, Security Information and Event Management (SIEM), or Extended Detection and Response (XDR) tools.
The Anti-Cloud Difference
The Anti-Cloud Service combines the convenience of cloud services with security of a hardened, on-premises datacenter, run by seasoned Information Technology (IT) experts. We're paranoid about your security and obsessive about your performance.
We thoroughly vet all the equipment we provide you with and carefully silo it to ensure all physical and network access is fully locked down. We do not have access to our client's data; all client data is always fully encrypted and inaccessible within the network, compute and storage components of the Anti-Cloud Service.